Sometimes, updates come out unexpectedly and turn out to be more buggier than previous builds. It’s true that no software is perfect, however, failing to upgrade means you’ll miss out on improved functionality and, more importantly, leaves you open to huge security risks in your network. What risks?
Botnet attack
Perhaps you recall the 2016 DYN Cyberattack?
On October 12, 2016, a massive distributed denial of service (DDoS) attack left much of the internet on the U.S. East Coast inaccessible.
That attack was powered by something the internet had never seen before: an army of over a million hacked devices, mostly internet-connected cameras.
The digital assault surpassed 660 Gbps of traffic, making it one of the largest recorded in history in terms of volume.
Such news is becoming commonplace as the number of attempted breaches and the sophistication of hackers are growing each year. At the same time, a flood of insecure IoT devices is drowning the Internet, everything from connected ICS/SCADA systems, routers, and cameras to security systems.
How do attackers find vulnerable devices on the Internet?
Shodan search engine
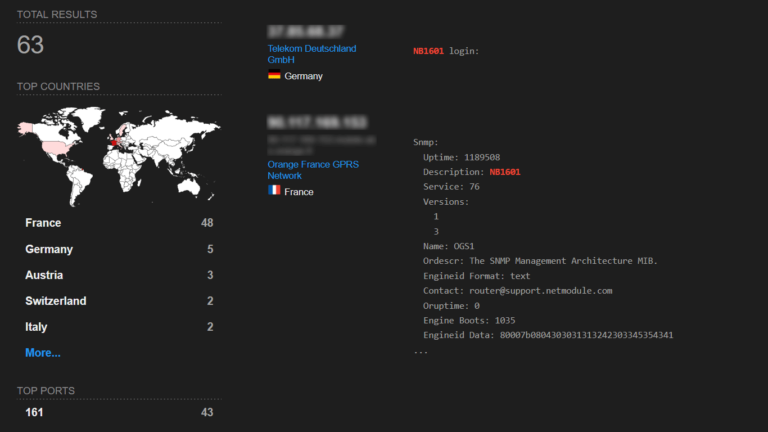
Queue Shodan (https://www.shodan.io/).
A search engine for everything connected (and that often shouldn’t be) on the internet, indexing pretty much anything and everything you could imagine — webcams, SCADA systems, refrigerators, medical devices, smart TVs, traffic lights, wind turbines, license plate readers.
Searching over nearly a billion devices to identify vulnerable systems, Shodan is of particular use for “skilled computer experts”. It scans the entire Internet and parsing information returned by various devices. Using that information, Shodan can tell you things like what web server (and which version) is most popular, or how many ports are enabled on the device, and what make and model the device may be.
Protecting yourself
Password selection
Many devices publicly announce their default passwords in their banner. For example, Cisco often advertises a default username/password combo of “cisco/cisco” for their devices. So yes, it seems obvious, but immediately identifying any such default passwords like this on your network before attackers would be a good idea.
Private Network
When you connect to the network through a VPN, the data is kept secured and encrypted. Access to ports can be limited to the VPN interface protecting from external attacks by closing them off from the Internet.
Firewall
There is usually no reasonable reason for someone on the Internet to be able to access your routers. It is important to have filters on the router to prevent unauthorized users from being able to log in to the router, or to send management traffic to the router.
You maybe wondering at this point, “why am I doing all the work?”
Whose responsibility is it?
Sure, customers often fail to ask for strong cybersecurity features for devices. However, manufacturers are also guilty of abandoning support of their equipment, leaving consumers stranded with insecure devices all the while assuming the best.
Ultimately, the question is why are so many vendors willing to supply equipment without doing their due diligence on the product software?
Aliexpress, Alibaba and Banggood websites are filled with manufacturers selling hardware solutions with no information on the software, or reference to any open source code used on their products.
So what should you consider before buying?
Firmware updates
Many people look at the glossy technical brochure and select a product based purely on the physical hardware specification, but the software is becoming an essential factor.
As previously mentioned, firmware updates work to identify and rectify embedded security vulnerabilities. This support is required throughout the device’s entire life-span.
Some questions to ask a future vendor
- How often do you actually update your software?
- How long will you provide software updates for the product?
- Are the updates for the product free for life?
- Do you have a dedicated resource to review CVE updates to identify possible security vulnerabilities?
Are any other factors to consider?
Release notes
Release notes tell customers about all of the hard work the manufacturer did to make the product a little better.
The information in each new version release tells us whether or not an update is important or urgent. Especially relevant when you are managing a fleet of hundreds of devices.
Without release notes there is no way for customers to know the exact product updates, or if the products even get updated.
Lack of release notes makes a statement about what a company thinks of its user base – that their users don’t care about software updates, so why bother?
While cost and lead-times are crucial on any project, in this age of cyber threat it’s imperative we remain alert to the embedded security risk in our networks.
Select devices with regular software updates, and keep them from joining a zombie botnet army.





